- Home
- People
- Projects
- Practical Security Verification
- Secure Cloud Computing
- Security of AI Systems
- Deep Learning for Security
- Smartphone Security
- Cache Side-Channels and Secure Caches
- De-anonymization
- Running Unvetted Programs
- Secure RISC-V processor
- SP and Bastion Secure Processor Architectures
- Crypto Acceleration
- OpenSPARC Researh
- SecureCore
- Advanced Bit Manipulation
- PAX
- PLX
- Publications
- Research
- Conference and Journals
- Project Archive
- Photos
Research
PALMS research is currently focussed on security-aware computer architecture and the design of trustworthy computer systems.
Research Areas
Below are some sample research areas:
- Security focus: Hardware-enhanced Security
- Confidentiality, Integrity and Availability
- trustworthy computer architecture for secure & resilient systems
- multicore security; SOC security; clients and servers; embedded systems
- What hardware trust anchors can significantly improve security?
- Secure Cloud Computing
- secure virtual machines; trust evidence to cloud customer
- How can you trust processing and storing sensitive data in the Cloud?
- Mobile security
- e.g., smartphones, wireless key management, mobile cloud computing
- Architecture for Self-Protecting Data
- e.g., electronic medical records; analytics processed in Cloud; iPhone and Android apps
- Side channel Mitigation
- How can we design hardware that optimizes performance without leaking information? (e.g., cache side-channel attacks)
- Mitigation of Internet and wireless epidemics, e.g., DDoS
- Trust evidence and security verification
Research Projects
Below are some sample research projects:
Secure Cloud Computing
- How can you trust your confidential data to be processed or stored securely in the Cloud?
- including Secure Virtual Machines; Secure e-health; Secure sensor nets.

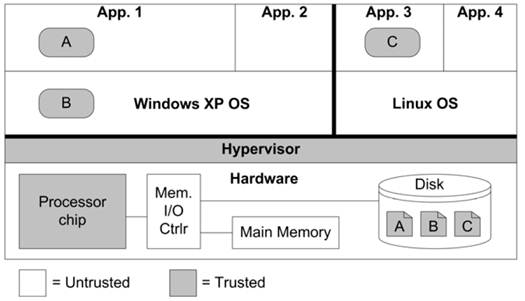
Secure Processor-Hypervisor Architecture
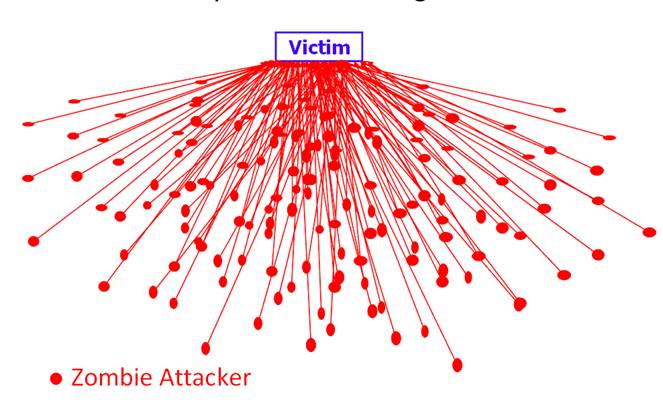
Early Detection and Mitigation of Distributed Denial of Service Attacks
Secure Hardware and Applications
- Best-in-class Performance and Power in design of secure hardware subsystems, e.g., Secure caches
- Secure Personal Health Records
- Secure Sensor Nets
Secure/Trustworthy Computer Architecture and Systems
- How can we design computers to be intrinsically more trustworthy?
- Including Multicore security; Embedded systems, SOC security; clients and servers
Architecture for Self-Protecting Data
- How can you allow untrusted applications to run using sensitive data without breaching confidentiality?
Side channels and Covert channels
- How can we design hardware that optimizes performance and power without leaking information? (e.g.,thru cache side-channel attacks)
Wireless (Mobile) Security
- How to prevent or mitigate wireless DDoS, worms or viruses?
- What security features to build into smartphones?
Rethinking Computer Architecture for Secure and Resilient Systems (NSF)
Our society, economy and national security are critically dependent on computers and computing devices. With a few hops, commodity computers and mobile phones can be connected to secret or sensitive information or to critical infrastructures. However, mainstream commodity computers have not been designed with security in mind, for the last three or more decades. Rather, they have been designed to improve performance, energy efficiency, cost or size, with security added on as an after-thought. While some specialized secure computers have been built, up to now, one had to sacrifice performance (or cost and convenience) for security. In this research, we explore what is feasible if we allow ourselves a clean-slate design, where security is a first-class goal, on par with performance and other goals. We will rethink computer architecture from first principles to significantly improve both the security and the performance of future computers. The research has two thrusts: how to design computer architecture to enable more secure software and systems, and how to design computer hardware components that are themselves more trustworthy. New architectural foundations for secure processing, secure memories, secure caches, secure virtual memory translation, secure storage, and secure control flow will be developed. The solutions will also consider hardware attacks, in addition to software and network attacks. The intellectual contributions of this research will be new architectural foundations, and a new dimension of "threat-based design" in the research and development of all future computers. The broader impact of this research is to provide core security technology that can be built into commodity computing devices and their servers. These can be used in computer, communications, control, entertainment and embedded systems to build significantly more secure systems.
Proposal Number: NSF CCF-0917134, PI: Ruby Lee
SecureCore for Trustworthy Commodity Computing and Communications (NSF, DARPA)
Collaborators: Ruby Lee (Princeton), Cynthia Irvine (NPS), Terry Benzel (USC-ISI), Mung Chiang (Princeton). The SecureCore project will investigate a secure integrated core architecture for trustworthy operation of mobile computing devices. This core includes a security-aware general-purpose processor, a small security kernel and a small set of secure communications protocols. The research will use a "clean slate" approach to define a minimal set of fundamental architectural features required for such a secure core, for use in resource-constrained, ubiquitous computing platforms exemplified by secure embedded systems (e.g., computer in a heart monitor) and mobile computing devices (e.g., handheld web-enabled computer). This approach shows what is possible when security is designed in at the beginning rather than added on as an after-thought. It also changes the computer design paradigm from an emphasis on performance to one on trustworthy, dependable operation. The goal is to achieve the desired security levels without compromising performance, size, cost, energy consumption, or usability. Threat models will be re-examined in the new context of continuously networked commodity devices and Internet-scale epidemics. The broader impact is to provide the scientific basis for trustworthy computing, communications and storage in pervasive computing environments. SecureCore impact will be immense if its architecture influences the design of future trustworthy commodity products, as well as the curriculum for computer hardware and software engineering education.
Proposal Number: NSF-0430487
Toward Supercomputer Performance for Advanced Bit Manipulations on Commercial Microprocessors
Certain important applications demand very fast, advanced bit-level manipulations, like arbitrary bit permutations, bit matrix multiplication and transpose, that are not well handled by current word-oriented microprocessors. These applications include bio-informatics, genomic decoding, code discovery, code breaking, cryptography, cryptanalysis, biometrics, multimedia processing and other applications. In the past, super-computers have been built for some of these purposes. With the rapid performance improvements in today's commercial microprocessors, we believe we can potentially achieve the performance of such supercomputers by judiciously adding a few new instructions and features to general-purpose processor architectures and making use of available parallelism at appropriate levels.
This project proposes to investigate how very fast bit manipulations can be achieved in general-purpose, word-oriented processor architectures. We will consider what instructions or other features could be added to a high-performance 64-bit microprocessor, such as IA-64 or a typical RISC instruction-set architecture (ISA). We will consider how the performance can scale with larger word sizes (increased bit or subword parallelism), increased instruction-level parallelism (ILP), more registers, and multiple processors. We hope to optimize for the set of bit operations, rather than for each one individually. This optimization will also take into account the features provided by the base architecture. Our goal is to achieve unsurpassed performance for advanced bit manipulations that is extremely cost-effective since it uses commercial microprocessors and is scalable. For the ideal processor, designed from scratch, we shoot for a Cray on a chip (or better), at a fraction of the cost.
ITR: Architectures and Design Methodologies for Secure Low-Power Embedded Systems (NSF)
Embedded systems, for example in information appliances and networked sensors, face some of the most demanding security concerns - they are resource constrained while frequently needing to handle sensitive information in physically insecure environments. Security processing can easily overwhelm the limited computation and memory resources of embedded processors, especially with the escalation in the amount of data to be processed and the data rates of high-speed networks. This "performance gap" is compounded by the "battery gap", which is the disparity between energy requirements and slow improvements in battery technology, for secure low-power embedded systems. This project is an inter-disciplinary study of several core technologies that will enable the design of secure, low-power embedded systems. It spans the fields of security, cryptographic algorithms, embedded processor architecture, computer arithmetic, low power design, and enabling design methodologies and tools. It addresses the performance, energy and security requirements, and their tradeoffs, in embedded processors and systems. The research goals include a comprehensive analysis of the performance requirements and power consumption for security in embedded systems. The project is developing efficient architectures for security processing in low-power embedded systems, including configurable security modules for system-on-chip designs, and architectural guidelines for tiny cryptographic processors for embedded systems. The performance, power and security tradeoffs based on customizations at the protocol, cryptographic algorithm, and hardware and software implementation levels are studied. Design methodology and tools include processor design tools to facilitate the design of new security processing architectures based on open frameworks such as the PLX (hosted at Princeton) and SimpleScalar toolkits. The project explores domain-specific design methodologies that jointly co-design security protocols and processing architectures to meet the required security, performance and power priorities and constraints. The research enables the design of embedded systems with higher levels of security, while achieving an order of magnitude or more in performance and battery life, compared to conventional approaches. Broad security impacts are expected for embedded system design, in addition to impact for future research and education. Results are disseminated to industry through the Princeton Architecture Lab for Multimedia and Security (PALMS) and the NJCST Center for Embedded System-on-a-Chip Design. The research results are being woven into graduate and undergraduate courses.
Architectural Solutions for Preventing Distributed Denial of Service Attacks (NSF)
Denial of service attacks flood a web-site with so many requests that it can no longer respond. Computers connected to the Internet are vulnerable to being used unwittingly in mounting a distributed denial of service (DDoS) attack on a victim web-site. Past countermeasures based on software patches or re-compilation are often ignored by users, leaving many systems vulnerable. This research first proposes a classification of the various denial of service attacks and countermeasures, then defines architectural solutions in the core (non-optional) hardware and software of future machines. The vulnerabilities of computers, which allow DDoS attack networks to be set up, are studied. Low overhead architectural features in the core hardware of computers are investigated which hinder attack networks from being set up in the first place, or detect and prevent the execution of potentially hostile code. Malicious parties often employ buffer overflow attacks to gain entry to a computer by corrupting procedure return addresses. This research investigates features like a secure return address stack (SRAS) in the processor architecture as a new defense against such buffer overflow exploits. The proposed research approach is unique in providing defenses in the client platforms rather than only in the servers or routers, and in building more trusted architecture in the core hardware, rather than only in software layers. Since application code need not be changed nor re-compiled, both legacy and future software can enjoy the security benefits of hardware architectural solutions. Since DDoS attacks pose a serious threat to the availability of critical Internet services, this research can contribute to the overall security of the Internet while increasing the trust that owners may have in their interconnected information appliances.
Instruction Set Architecture for Pervasive Security (NSF)
This research investigates core architectural features for secure and private communications and computations over the public Internet and wireless infrastructures. It focuses on what instruction-set architecture (ISA) features general-purpose processors would have, if secure information processing is the default pervasive mode of operation, with non-secure processing the optional mode, rather than vice versa. It proposes ISA features for very fast, flexible, software cryptographic processing, not only for current algorithms but also to enable algorithm designers to create new cryptographic algorithms that are more secure and more efficient. Word-oriented, programmable processors can be radically more effective for cryptographic functions with new instructions for sub-word manipulations, as well as for multi-word arithmetic. Novel bit permutation instructions are proposed for providing superior diffusion capabilities for current and future symmetric key algorithms. Their performance, area and latency tradeoffs, and scalability with superscalar organizations are studied. Very fast table lookup and other ISA features are also studied for algorithms like Rijndael, the recent Advanced Encryption Standard winner, and for public-key algorithms like Elliptic Curve Cryptography. The research also investigates architectural features for secure key management, and other ISA features designed to enhance or enforce system security.
PALMS Technology
- Secure high-performance caches
- Unlike existing caches, our Newcache architecture does not leak information through software side-channel attacks, and at the same time improves performance and power!
- Secure Processor technology
- SP and Bastion architectures enable trusted applications even with malware in the system and a compromised O.S.
- Advanced Bit Manipulation Instructions and Modules
- Accelerates crypto, multimedia, wireless applications that are bit-oriented rather than word-oriented (for processor or FPGA)
- Instructions adopted by Intel microprocessors in Intel Advanced Vector Extensions Architecture, June 2011.
- General-purpose crypto acceleration primitives
- Fastest AES cipher performance, in software or FPGA, comparable to special-purpose ASIC, but also useful for many other algorithms including communications and multimedia.
- Towards “No-overhead Crypto Processing”
